N@TM Blog
Night At the museum blog detailing code explanations
- Encrypter/ Decrypter Algorithm
- PLanning for the project
- Diagram of how the encrypter encrypts raw data
- Algorithm Code Explantion
- 1. Creating databses coloumns and a dictonary
- 2. Encrypting data using the first layer of encryption, the ceaser cipher
- 3. Creating a matirx of words for 2D iteration
- 4. Reverse string swapping
- 5. Vowel and special character swap
- Working Tree of the code
Encrypter/ Decrypter Algorithm
The encrypted decrypter algorithm focuses on as the name suggests encrypting and decrypting text. The algorith mis mostly backend fucntional, which means that the frontend sends the data to the backend and the backend databse encryptes said data and stores a multiude of varibles realting to said data in the backend databse. It works like this the frontned databse sends the data to the backend databsae wherein the algorithm works to encrypt the data uinsg a 4 layer encryption algorithm. Tha algorithm first encrypts the data using a ceaser cipher, then is sorts is laphbetically, then is swpas the first and last letters, then the algorithm swithces vowels for speacial characters. This multi layer algorithm works towards encryptingdata in a way that is almost impposbile to decypt without a special key that includes how the creaser cipher is shifted. The number of letters the ceaser cipher is shifted is whatt he previous sentnces means.
PLanning for the project
Together with my teacm mate Ryan, we planned to compelte this complex projct is about two weeks which thus took a lot of planning and methoidc work in order to compelete the project. Here are the plans below.
Encrypter and Decrypter
In our final project, we plan to create a symmetric encrypted and decrypted algorithm that encrypts and decrypts code in a specific key. We plan to either generate a key or use the ASCII key to encrypt and decrypt text. Our UI functions as follows- the user inputs text and clicks a button that sends said text to the backend API. Once the text is sent, the backend has code that will encrypt the data and store it in the database. The encrypted data is then sent to the frontend UI wherein the code decrypts the text. Since a backend network is involved we most likely plan to create a symmetric algorithm wherein the presence of a public and private key creates a more secure system. We also plan to provide the user with a secret message each time they send data to be encrypted to help with the sorting and searching algorithms. The secret key would assign each word of the data with a specific number according to their initial arrangement and when the words are mixed it would be easy to decrypt the messaging on the front end.
Feature Flowchart
- User input from the front which includes raw data
- Raw data is posted to the backend database wherein it is encrypted using the symmetric ASCII key
- Raw data and encrypted data are stored in a backend database along with an ID/Keyname
- Data is sorted according to the ID
- Back to the frontend
- The user requests data from the backend/ the encrypted data using the ID/Keyname
- Algorithm searches across the database to identify the ID number and sends the data to the frontend.
- Encrypted data is displayed and using a decryptor the data is decrypted into the original raw.
Features and Requirements Breakdown
1. Loops (Algorithmic) Show a specific example of building a List using List Comprehension. Show examples of processing a list using conventional and for each method. The list we plan to use is the ASCII key list or our key which contains values that are both in the English alphabet and its corresponding numbers and letters. This list shall be part of the backend and frontend code wherein the system encrypts the text. Given that the program uses a backend we also plan to store said data both as the input data from the user and the encrypted data from the algorithm.
2. Sorting / Searching (Algorithmic) Show examples of sorting and searching using the backend of your project. FYI, SQLAlchemy allows filtered selections and sorting. Additionally, you have sorting options discussed in the tech talk. The backend of the algorithm shall search through the data given by the user to look for the letters and encrypt them with the values of the key. regarding sorting we plan to send the encrypted data as a mixed bag of words and numbers to the frontend system that then sorts the data once decrypts it providing another layer of security for the program system.
3. Big(O) Illustrate the Space and Time complexity used in your Sorting / Searching algorithm. The algorithm sorts words according to alphabetical order and thus the time taken would be decided by that issue.
4. 2D Iteration Show examples of code that uses 2D iteration. This can be anywhere in your code where you are using rows and columns. The roles and columns that would most likely be used in our code are from the key relating it to the alphabet present both in the fronted and the backend in order to both encrypt and decrypt the data sent from the user and back from the API.
5. Deployment (Full Stack) A complete deployment illustration of multiple people using and updating your Full Stack Web Application simultaneously. Use AWS deployment. Ensure the application supports multiple users by implementing user authentication and session management.
Tasks: Sri: Create frontend and backend code that determines how he data is encrypted and decrypted Ryan: Creat the sorting algorithm which creates the mixed bag of the encrypted data and re sorts it back in the frontend algorithm.
Sprint Schedule
Week 1:
- Establish frontend and backend servers, ensure CRUD operations function properly between both.
- Begin writing and formatting backend code, get and post requests
- develop procedures that encrypt user input, make algorithm that manipulates string, and code to decrypt the user input.
Week 2:
- finish frontend (html and js file) and backend (api and model in .py)
- Look through requirements to make sure we meet all criteria
- Deploy, ensure everything is functioning, properly prepared for NATM
Diagram of how the encrypter encrypts raw data
# 1. Encrypt using Ceaser Cipher
# Shift Value equals 5
# New string equals WDFS
#2. Encrypt using 2-D Iteration
# Create Matrix
# [W, D, F, S]
# Substritute the first and last and so on
# [S, F, D, W]
#3. Sorting the encrypted data alphabetically
# [S, F, D, W] to [D, F, S, W]
#4. Check for vowels
# Negetive no vowels, thus return false for vowels present
#5 Create encrypted_id
#India6-5
#6 Display Final result
# encrypted_id = India6-5
# Encrpted_data = dfsw
Algorithm Code Explantion
1. Creating databses coloumns and a dictonary
The code segment above shows how the code in th abackend creates a database with the different coloumns and the formation of a disctonary with the military alphabet. This military alphabet is then used to create the special id which is used to decrupted the dataorextract the raw data from teh database. This is an important step in teh program as this lays the foundation of the code and enbales the program to encrypt or decrypt the data.
military_alphabet = [
"Alpha", "Bravo", "Charlie", "Delta", "Echo", "Foxtrot", "Golf", "Hotel", #a list of the military alphabet from A-Z which is later used for the encrypted id name. The words are used in order to create a more prfessional look to the program
"India", "Juliett", "Kilo", "Lima", "Mike", "November", "Oscar", "Papa", # this is an example of a list being used in the program from which later parts are accessseed.
"Quebec", "Romeo", "Sierra", "Tango", "Uniform", "Victor", "Whiskey",
"X-ray", "Yankee", "Zulu"
]
class Record(db.Model):
id = db.Column(db.Integer, primary_key=True) # create a coloumn in the backend database for the id of the raw and encrypted data
raw_data = db.Column(db.String(512), nullable=False) # creates a backend coloumn to store the raw data sent by the user
encrypted_data = db.Column(db.String(512), nullable=False) # creates a couloumn which stores the encrypted data in the backend
shift_value = db.Column(db.Integer, nullable=False) # creates a couloumn that stores the value for the ceaser cipher shift value, usually an interger value
unique_name = db.Column(db.String(64), nullable=False) # stores the military alphabet randomly adssigned to the id and the raw data
encrypted_id = db.Column(db.String(128), nullable=False) # stores the encrypted id which is a mix of the id, shift value and the unquie name to form what will later be known as the secret key for decryption
vowels_present = db.Column(db.String(3), nullable=False) # New column for vowels presence, Y/N for the vowels present in the in string with is used to sort and subsitute values.
2. Encrypting data using the first layer of encryption, the ceaser cipher
The is the first layer of the encryption algorithm. This first layer encrypts data using a ceaser cipher shift value. This value is randomly generate value from 1-25 which enables the data to be shifted without repeatign the letters. This is the first layerof the encryption algorithm which acts as a beatuiful encrypting layer of the program.
def caesar_cipher_encrypt(text, shift): # This function encrypts text using a Caesar cipher with a given shift value. It iterates over each character, adjusting its ASCII value based on the shift.
encrypted_text = [] #Non-alphabetic characters are appended unchanged. This simple encryption demonstrates basic iteration and character manipulation.
for char in text: #Iterates over each character in the input text.
if char.isalpha(): # Checks if the character is an alphabet letter.
shift_base = 65 if char.isupper() else 97 #
encrypted_text.append(chr((ord(char) - shift_base + shift) % 26 + shift_base)) #Encrypts the character by shifting its ASCII value.
else:
encrypted_text.append(char)
return ''.join(encrypted_text) # Joins the list of encrypted characters into a single string and returns it.
3. Creating a matirx of words for 2D iteration
2D iteration in this code is used to process and manipulate elements within a 2D matrix. The swap_matrix_elements function demonstrates this by iterating over each row and then over each column within the row to swap elements, effectively reversing the order of elements in each row. This approach is utilized in the reverse_string_by_swapping_2d function, where a string is converted into a 2D matrix, the elements are swapped, and then the matrix is converted back into a string.
def create_matrix_from_string(text, width): #This function uses list comprehension to create a 2D matrix from a string, splitting it into chunks of the specified width
"""Create a 2D matrix from a string with the given width.""" # Creates a list of lists where in each row represents a matrix of the inputted text from teh user
return [list(text[i:i + width]) for i in range(0, len(text), width)] # Specifies the length and the width
def matrix_to_string(matrix): # This function concatenates rows and then joins the resulting strings to form a single string. It uses nested list comprehensions to process the 2D matrix efficiently.
"""Convert a 2D matrix back to a string.""" # Converts the matrix back into a string
return ''.join(''.join(row) for row in matrix) # joins the rows of teh matrix into one single string of letters
def swap_matrix_elements(matrix): # This function demonstrates 2D iteration by swapping elements within each row of a matrix.
#It iterates over the rows and columns, performing swaps to reverse the order of elements within each row.
"""Perform a 2D swap of elements in the matrix."""
rows = len(matrix)
cols = len(matrix[0]) if rows > 0 else 0 # This function iterates over each row of the matrix and within each row, it iterates up to half the width of the matrix.
for i in range(rows): # For each iteration, it swaps the elements symmetrically across the row. For instance, in the matrix
for j in range(cols // 2):
# Swap elements in each row
matrix[i][j], matrix[i][cols - j - 1] = matrix[i][cols - j - 1], matrix[i][j]
return matrix
4. Reverse string swapping
The sort_string_alphabetically function sorts the characters of a string in alphabetical order using Python’s built-in sorted function, which efficiently implements a sorting algorithm. It demonstrates simple sorting by converting the string into a list of characters, sorting them, and then joining them back into a single string. This approach leverages Python’s optimized sorting capabilities to achieve the desired alphabetical order with minimal code.
def reverse_string_by_swapping_2d(text, width=5): # This function combines creating a matrix, swapping elements, and converting the matrix back to a string. It showcases the practical application of 2D iteration in string manipulation.
"""Reverse the string by converting it to a 2D matrix and swapping elements."""
matrix = create_matrix_from_string(text, width) # Concantation of the string of letters into one single string of a word.
swapped_matrix = swap_matrix_elements(matrix) # The final result is the reversed string obtained after swapping elements in the matrix and converting it back to a string.
return matrix_to_string(swapped_matrix) # returns the result to the matrix
5. Vowel and special character swap
The replace_vowels_with_special_characters function replaces vowels in a string with specified special characters, using a dictionary to map each vowel to its corresponding special character. It employs a list comprehension to iterate over each character in the input string, replacing vowels based on the dictionary and leaving other characters unchanged. This approach ensures efficient processing and concise code while transforming the input string as specified.
def check_vowels_presence(text): # This function checks if a string contains any vowels, using a generator expression for efficient iteration. It returns True if any vowel is found, otherwise False.
vowels = "aeiouAEIOU" # this acts are teh searching segment of the algorithm which searches the encrypted string for the presence of any vowels, and if there are any vowels present then the vowel is interchanged into a special character
return any(char in vowels for char in text)
def replace_vowels_with_special_characters(text): # This function replaces vowels in a string with corresponding special characters. It uses a dictionary for mappings and a list comprehension for efficient processing.
vowels_to_special_chars = {'a': '@', 'e': '#', 'i': '$', 'o': '%', 'u': '&', # The searching portion of the algorithm
'A': '@', 'E': '#', 'I': '$', 'O': '%', 'U': '&'}
return ''.join(vowels_to_special_chars.get(char, char) for char in text)
Working Tree of the code
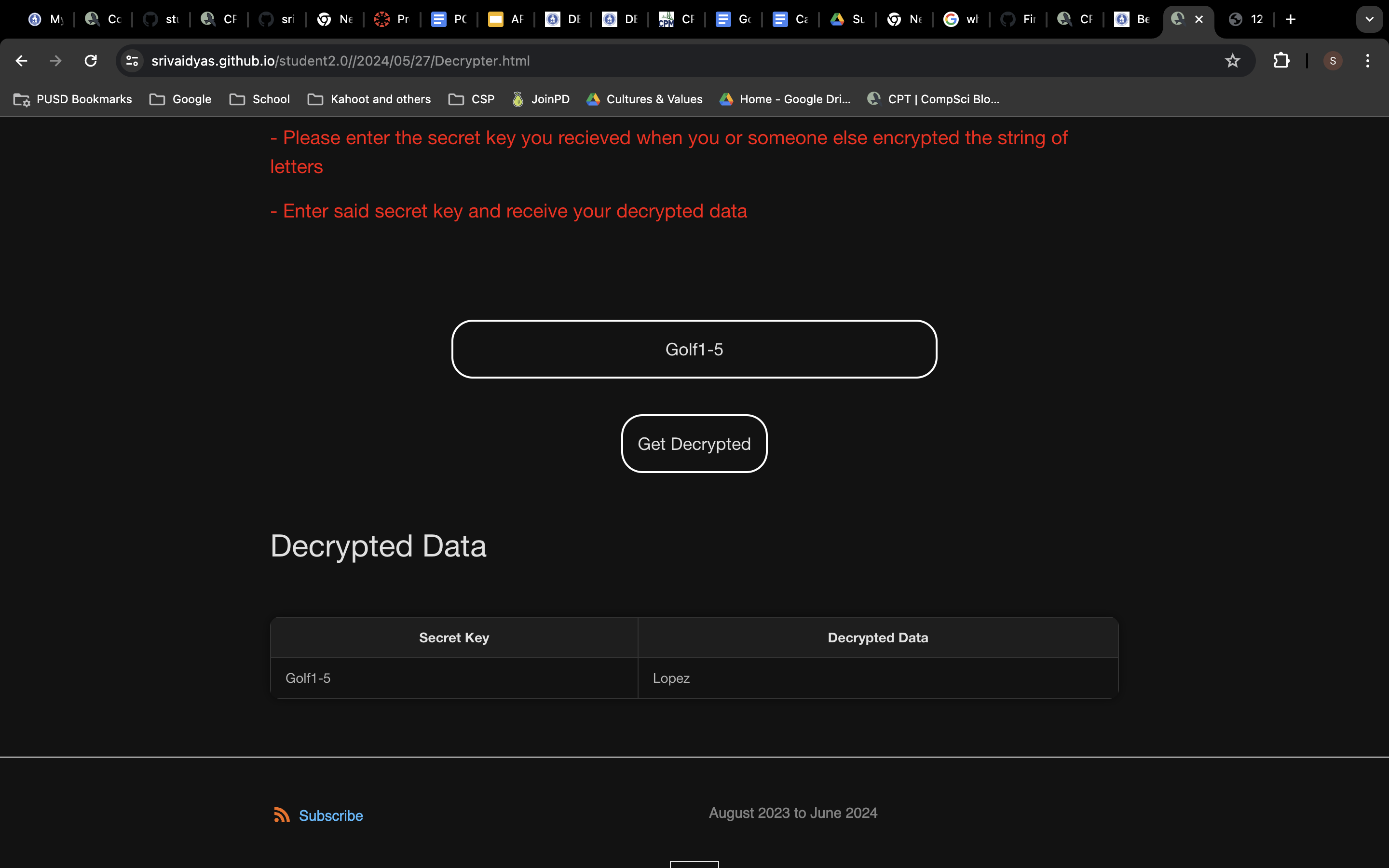
Intext data for encryption
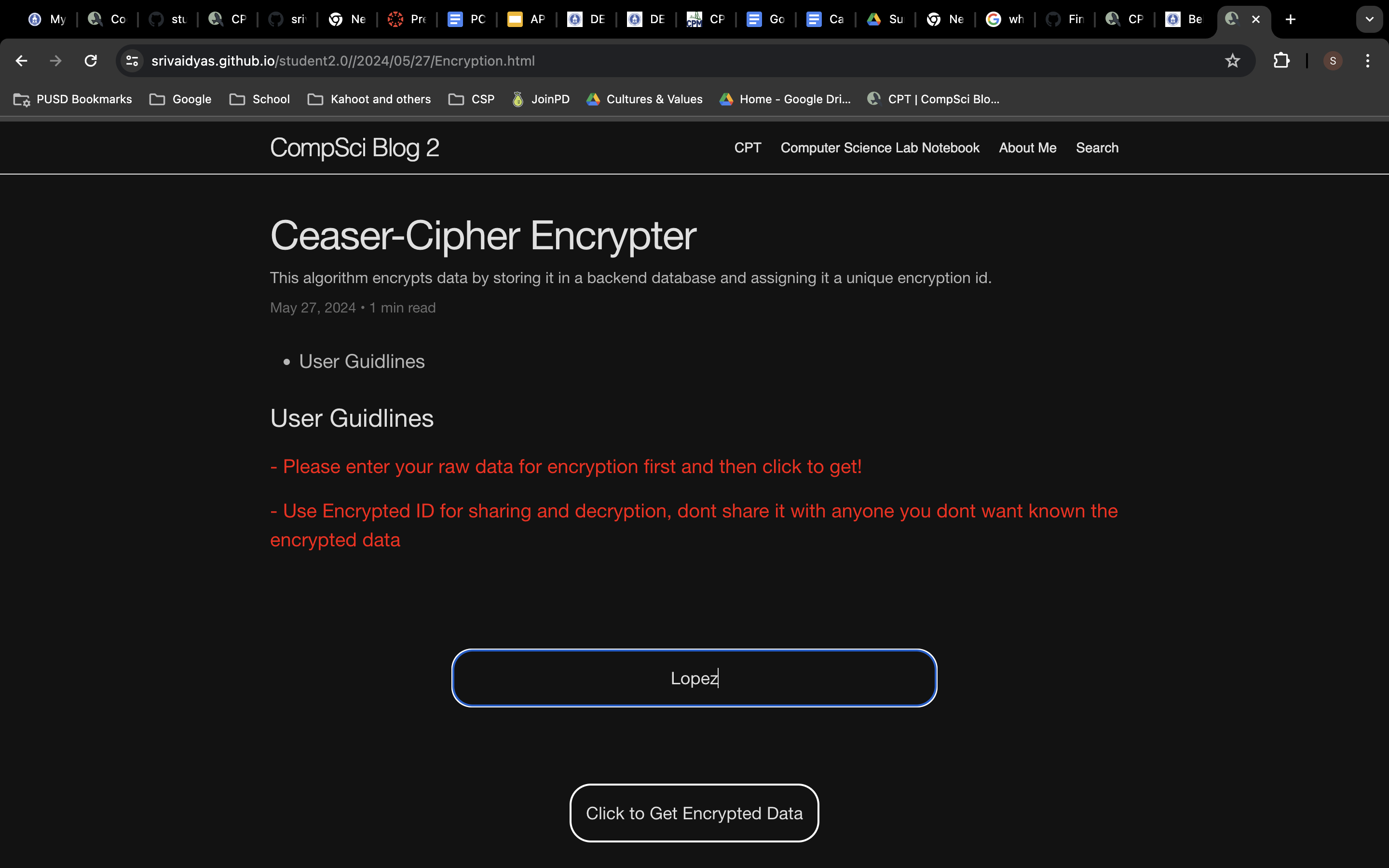
Sending data for encryption
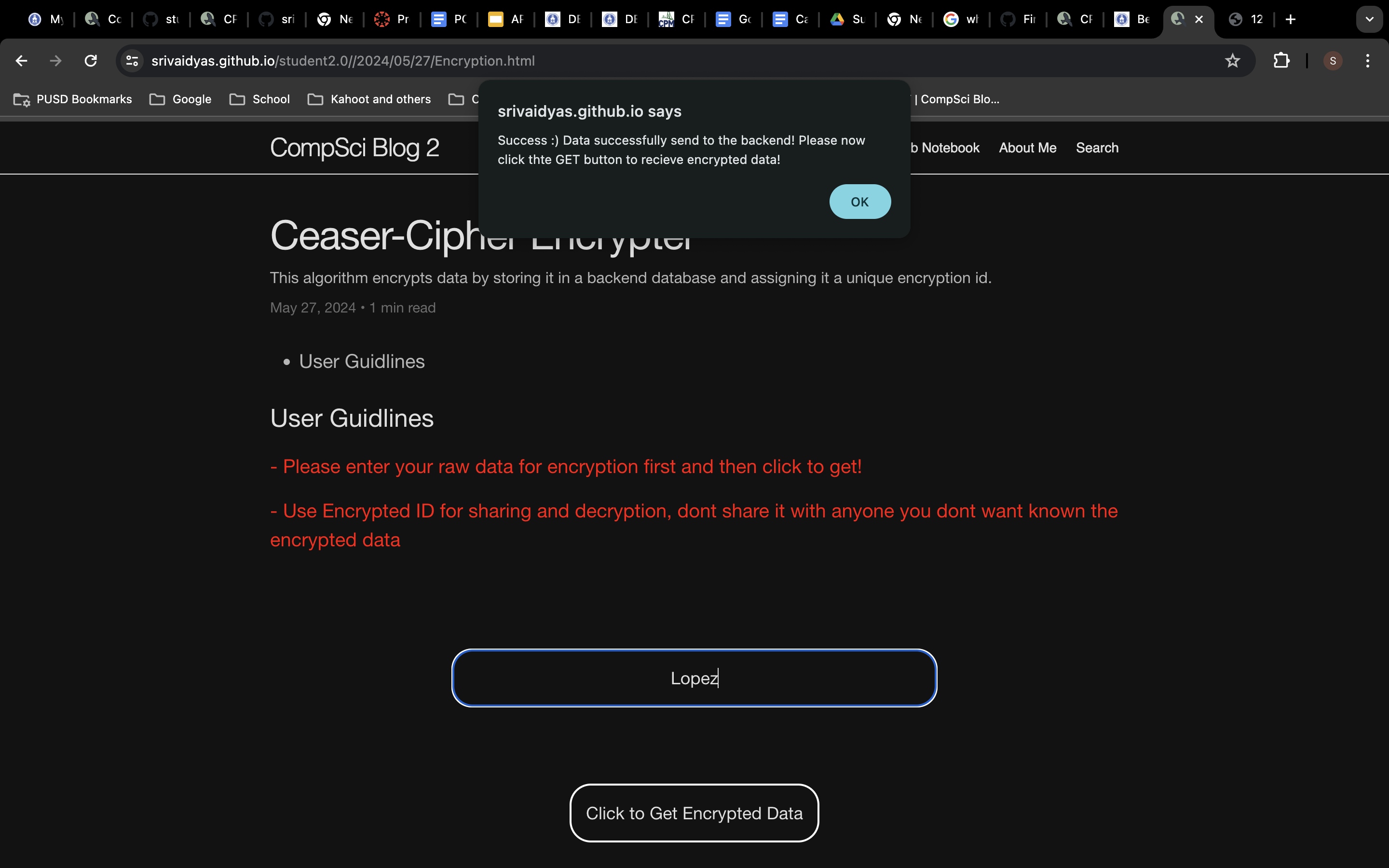
Visible data on the backend database
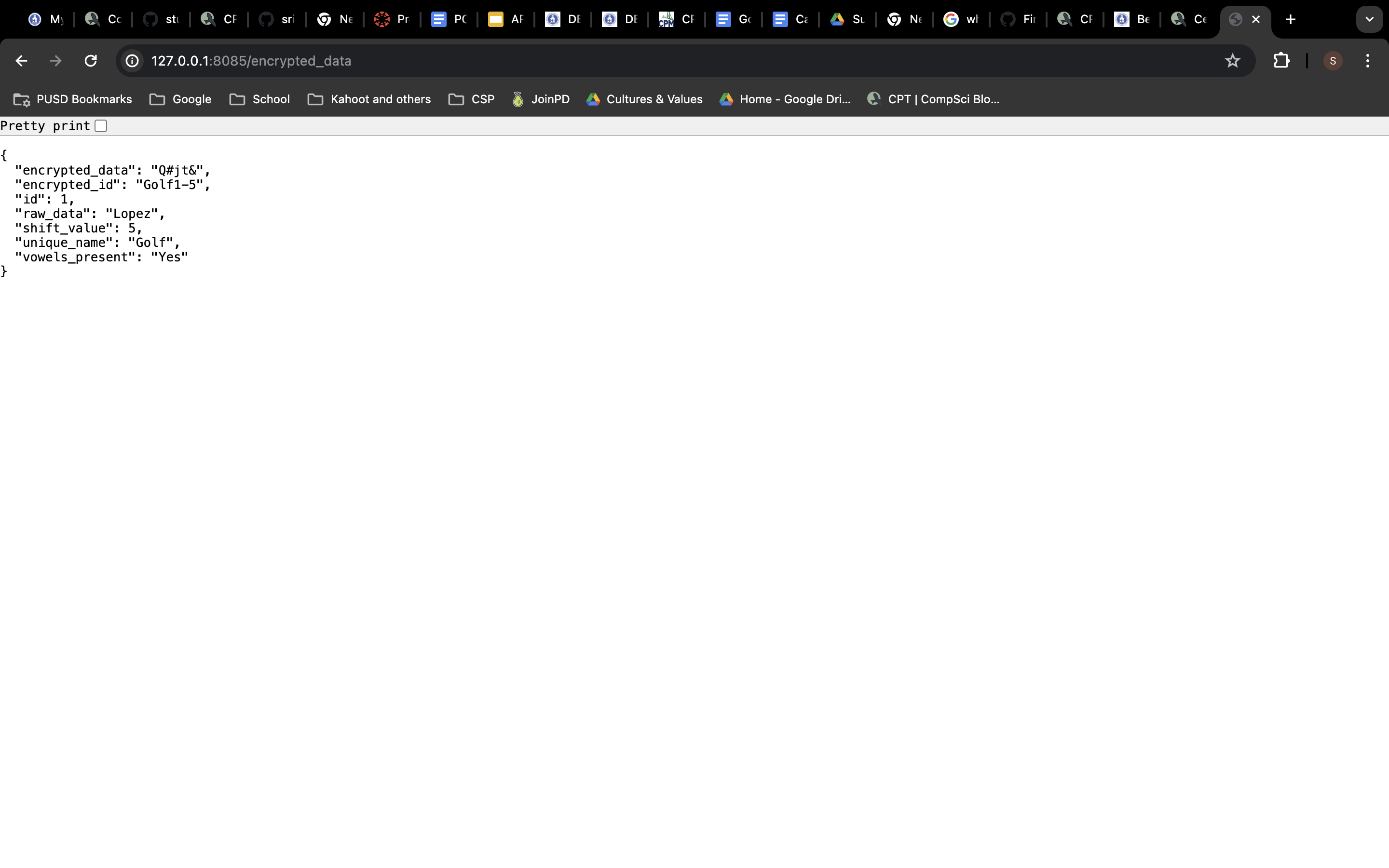
Getting the encrypted data and the encrypted id
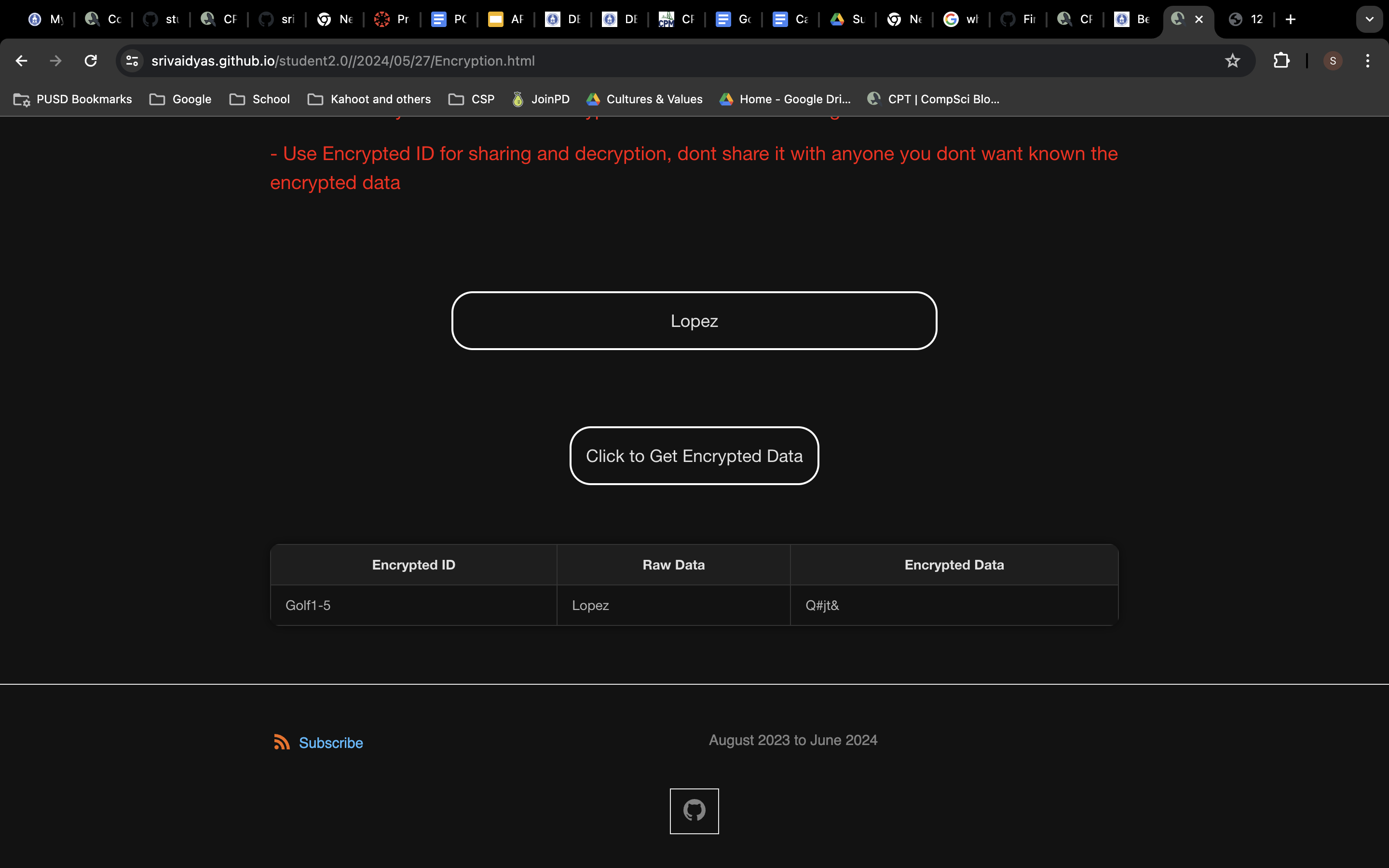
Using encrypted id to get raw data back in decypter